Nist 800 53 Template
Nist 800 53 Template - Simply put, if you run support or “supply chain” operation, the defense federal acquisition regulation supplement (dfars) made specific cybersecurity protocols a requirement. Vulnerability & patch management program. By establishing a framework available to all, it fosters communication and allows organizations to speak using a shared language. Web this publication provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the nation from a diverse set. Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf).
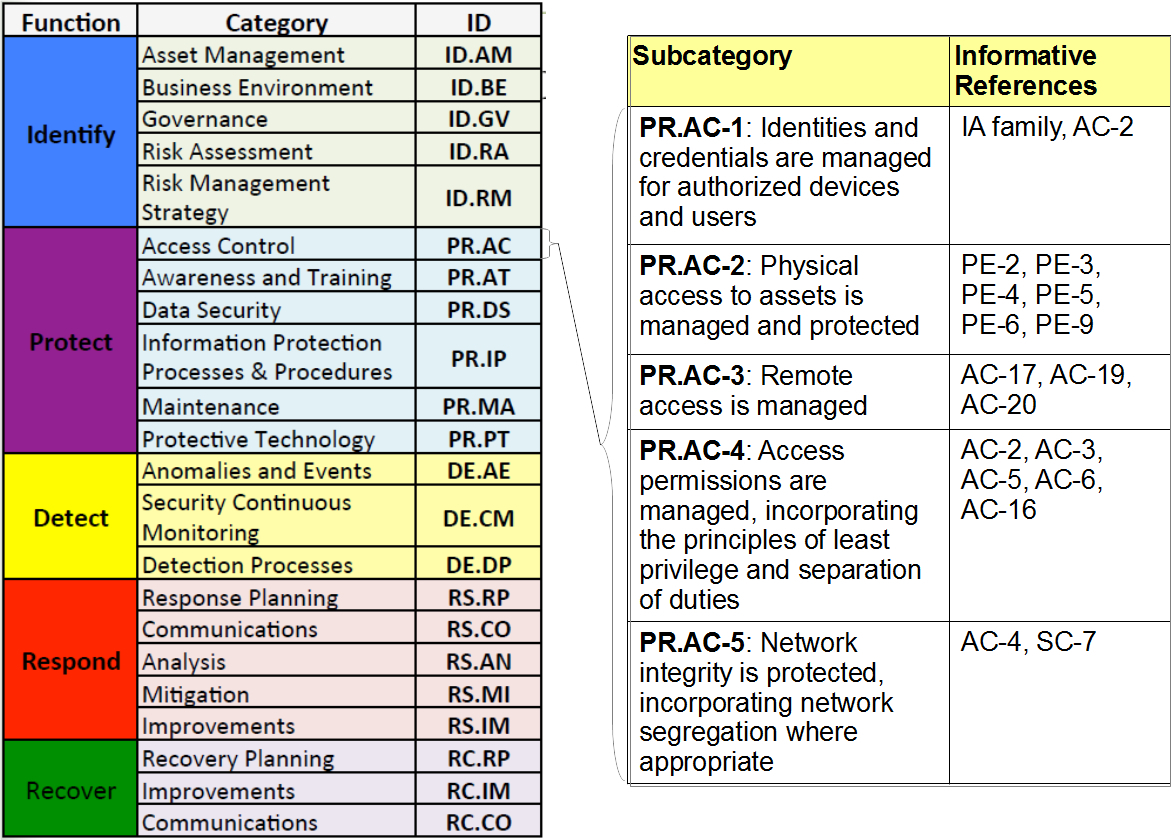
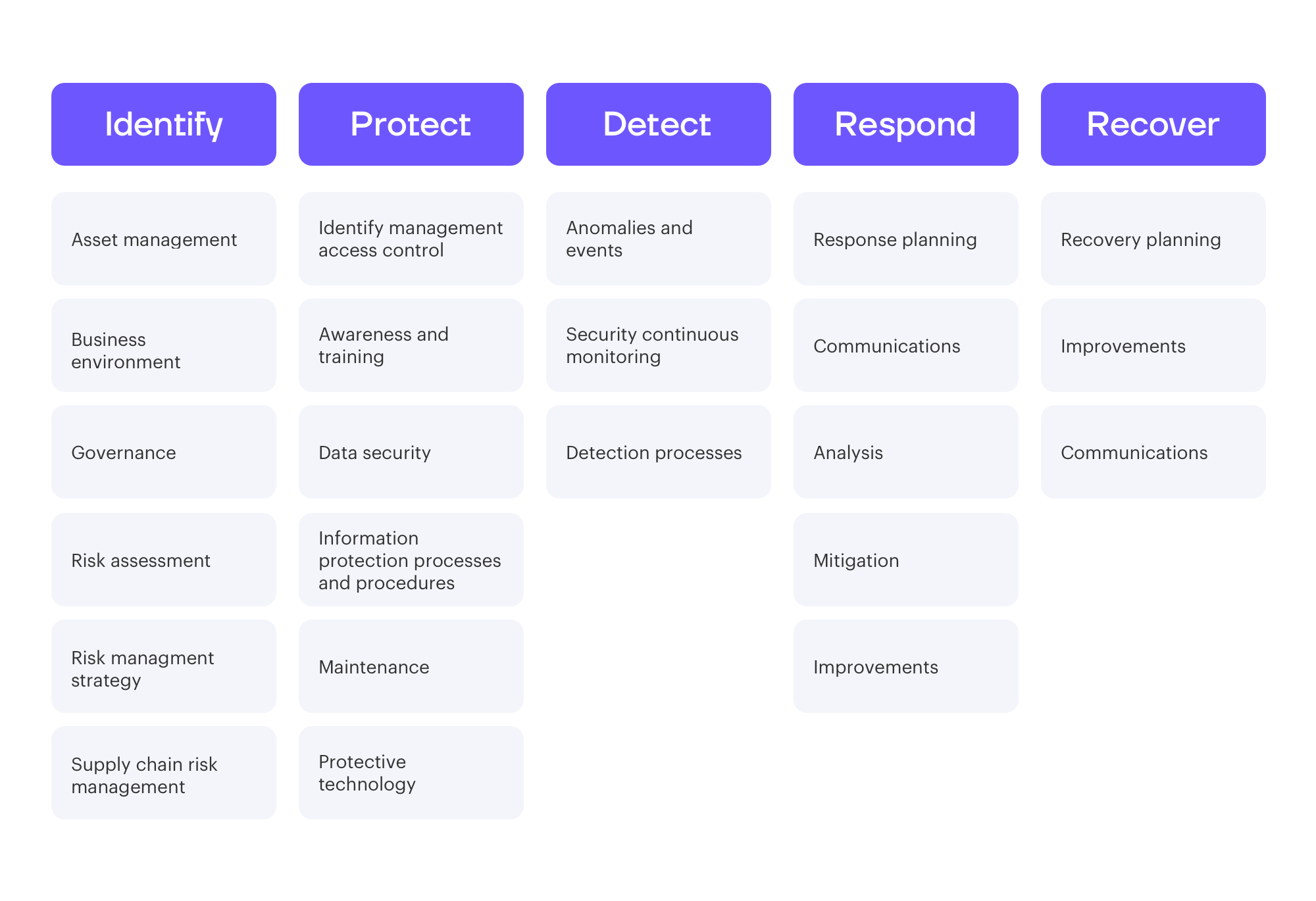
Risk assessment csf v1.1 references: Web last year, the department of health and human services’ (hhs) health sector cybersecurity coordination center (hc3) released a threat brief on the different types of social engineering 1 that hackers use to gain access to healthcare information systems and data. Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program collaboration to help ensure that the objectives of both disciplines are met and that risks are appropriately managed. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Federal information systems typically must go through a formal assessment and authorization process to ensure sufficient protection of confidentiality, integrity, and availability of information and information. Security and privacy controls for information systems and organizations. Target audience (community) comments point of contact informative reference submission form dependency/ requirement field name reference version
Nist 800 53 Risk Assessment Template Free Printable Template
2 the threat brief recommended several protective measures to. Web last year, the department of health and human services’ (hhs) health sector cybersecurity coordination center (hc3) released a threat brief on the different types of social engineering 1 that hackers use to gain access to healthcare information systems and data. Security and privacy controls for.
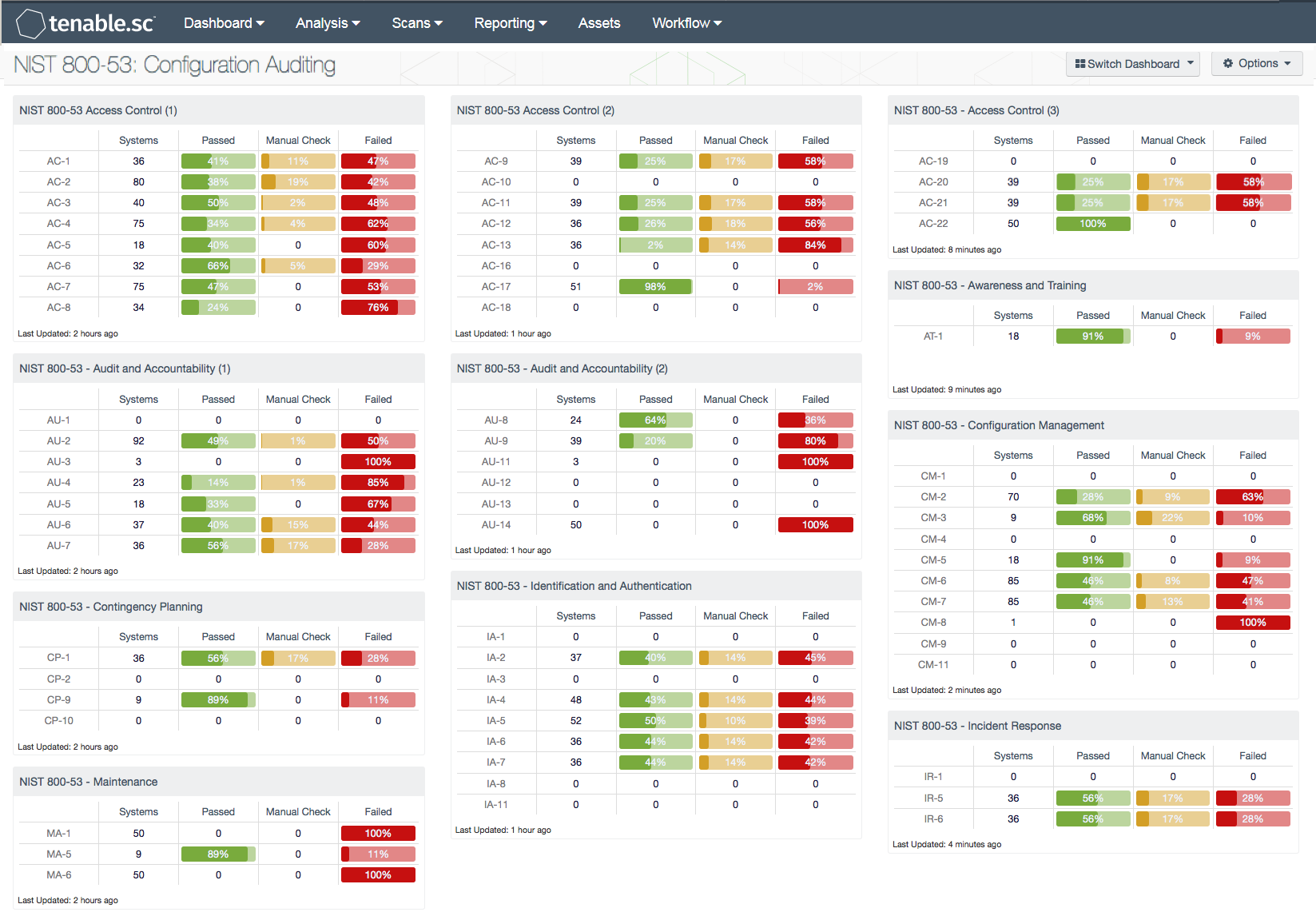
NIST 80053 Family Reports SC Report Template Tenable®
Web last year, the department of health and human services’ (hhs) health sector cybersecurity coordination center (hc3) released a threat brief on the different types of social engineering 1 that hackers use to gain access to healthcare information systems and data. By establishing a framework available to all, it fosters communication and allows organizations to.
Nist 800 53 Risk Assessment Template Master of Documents
This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Security and privacy controls for information systems and organizations. Web last year, the department of health and human services’ (hhs) health sector cybersecurity coordination center (hc3) released a threat brief on the different types of social engineering.
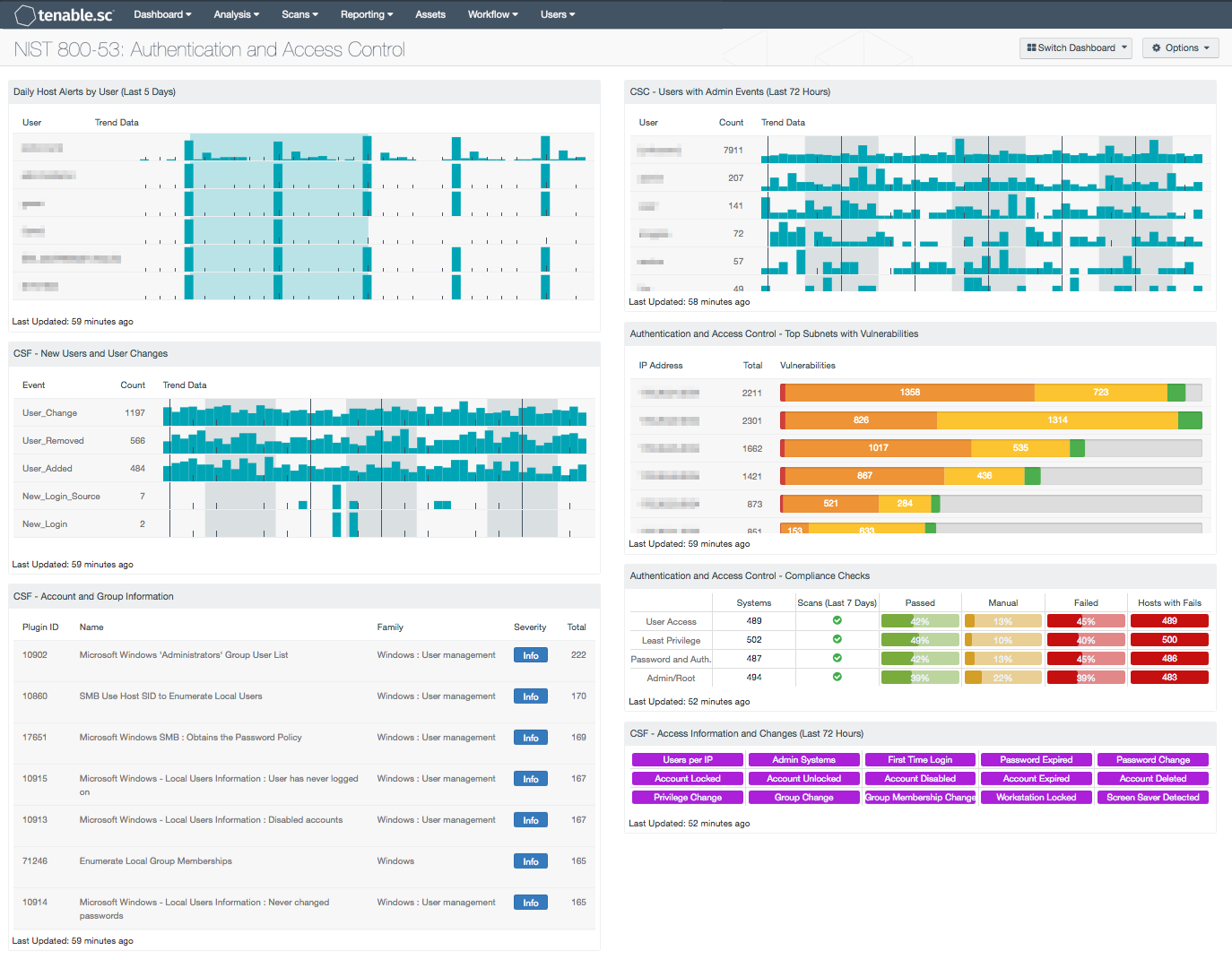
NIST 80053 Authentication and Access Control SC Dashboard Tenable®
Web 0 1 2 3 4 5 6 7 8 9 10. Risk assessment csf v1.1 references: Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). Prior to the 2.4 branch, a template functionality which allows users to create templates allows them to execute any code on.
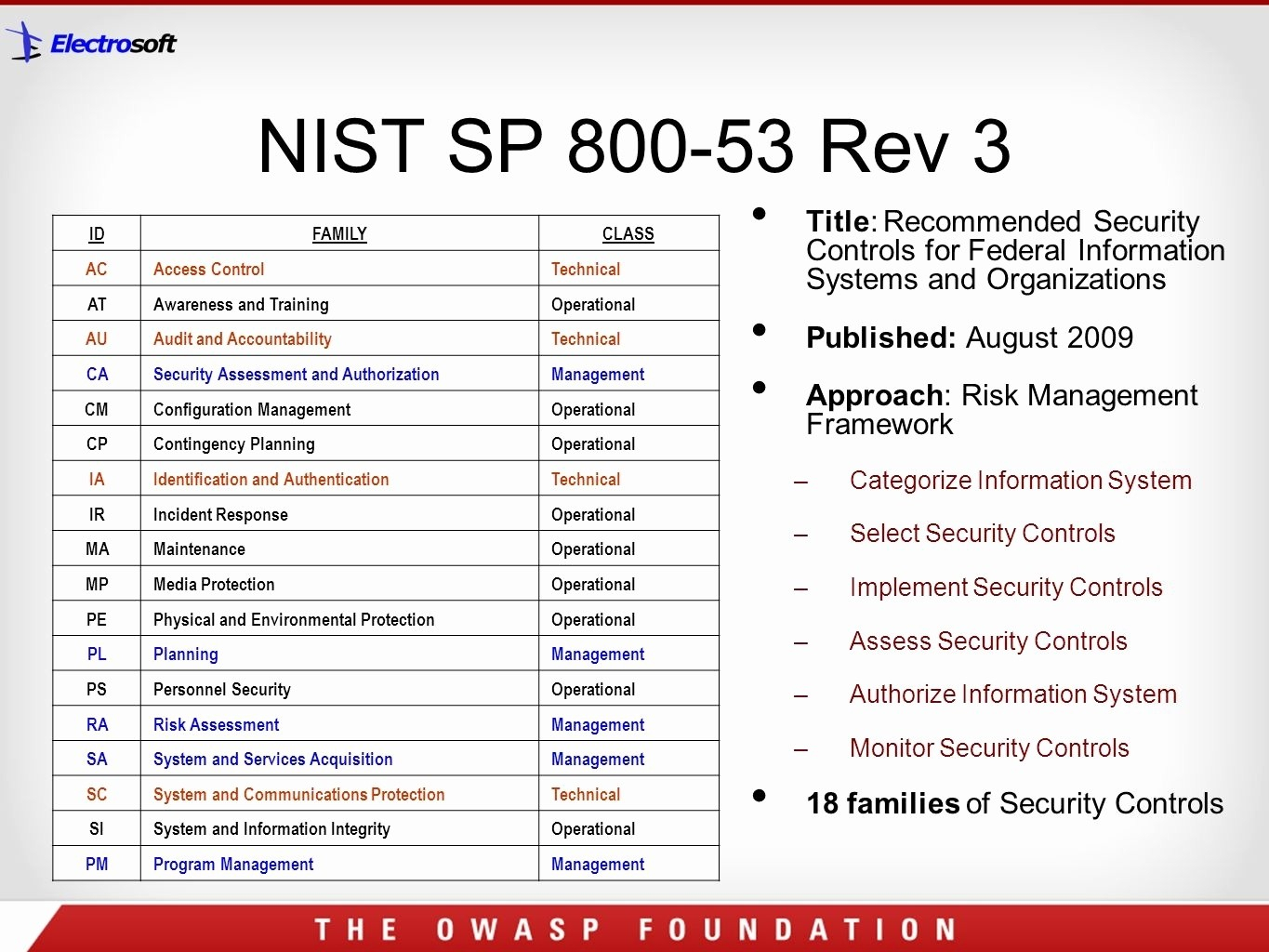
Nist Sp 800 53 Rev 4 Spreadsheet —
Web last year, the department of health and human services’ (hhs) health sector cybersecurity coordination center (hc3) released a threat brief on the different types of social engineering 1 that hackers use to gain access to healthcare information systems and data. Web security and privacy control collaboration index template ( excel & word) the collaboration.
Nist Sp 800 53 Rev 4 Spreadsheet Spreadsheet business, Business
Web joint task force abstract this publication provides a methodology and set of procedures for conducting assessments of security and privacy controls employed within systems and organizations within an effective risk management framework. Risk assessment csf v1.1 references: Federal information systems typically must go through a formal assessment and authorization process to ensure sufficient protection.
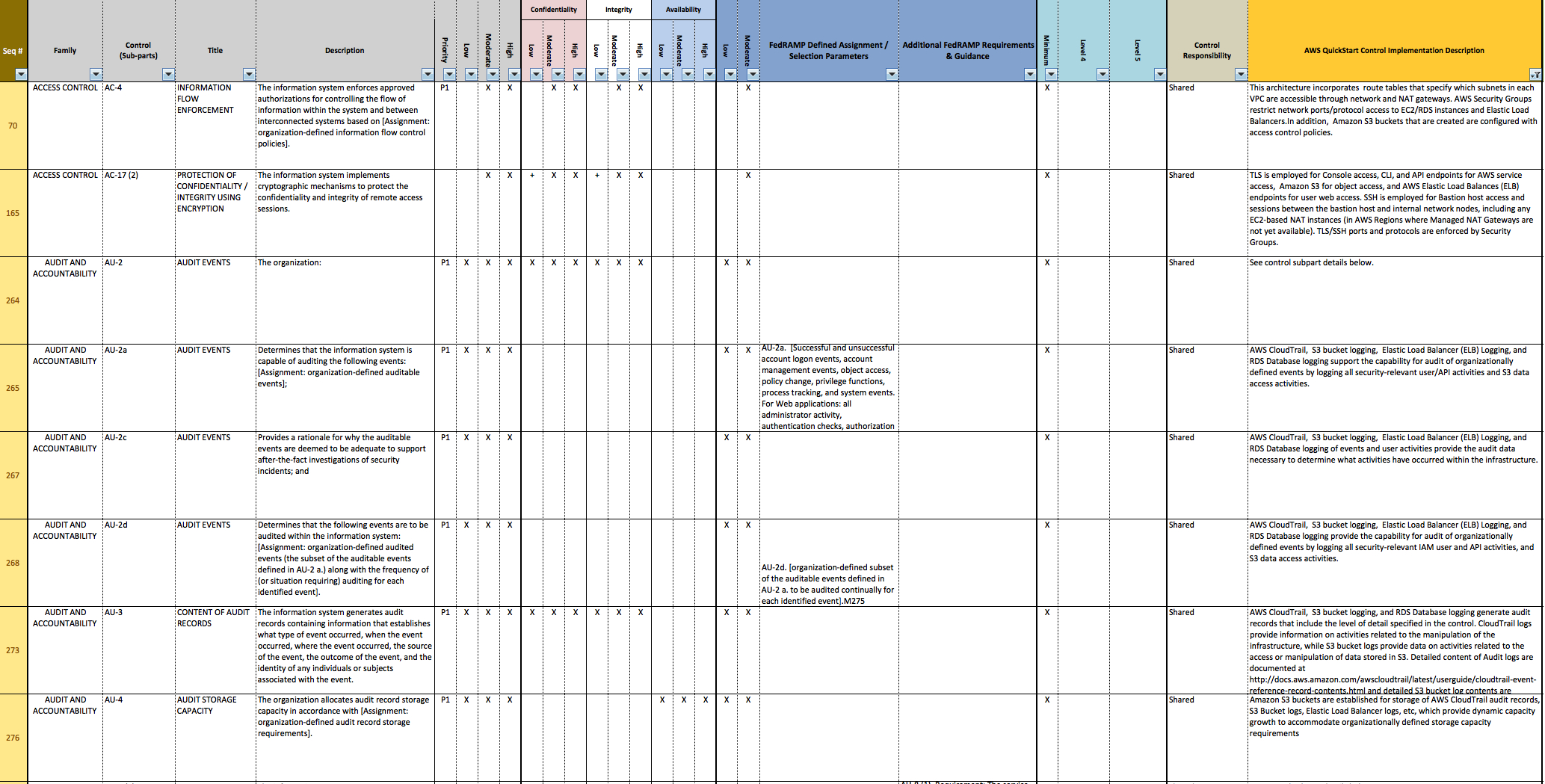
Nist 800 53 Rev 5 Controls Spreadsheet —
Web this publication provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the nation from a diverse set. Target audience (community) comments point of contact informative reference submission.
Nist 800 53 Security Controls Spreadsheet Google Spreadshee nist 80053
Federal information systems typically must go through a formal assessment and authorization process to ensure sufficient protection of confidentiality, integrity, and availability of information and information. This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. By establishing a framework available to all, it fosters communication and.
Nist 800 53 Rev 3 Spreadsheet —
Federal information systems typically must go through a formal assessment and authorization process to ensure sufficient protection of confidentiality, integrity, and availability of information and information. This publication is available free of charge from: 2 the threat brief recommended several protective measures to. Prior to the 2.4 branch, a template functionality which allows users to.
NIST 80053 rev. 5 compliance Qush blog
Web this publication provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the nation from a diverse set. Web joint task force abstract this publication provides a methodology.
Nist 800 53 Template Federal information systems typically must go through a formal assessment and authorization process to ensure sufficient protection of confidentiality, integrity, and availability of information and information. Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program collaboration to help ensure that the objectives of both disciplines are met and that risks are appropriately managed. Security and privacy controls for information systems and organizations. Target audience (community) comments point of contact informative reference submission form dependency/ requirement field name reference version Web joint task force abstract this publication provides a methodology and set of procedures for conducting assessments of security and privacy controls employed within systems and organizations within an effective risk management framework.
The Publication Itself States It.
2 the threat brief recommended several protective measures to. Simply put, if you run support or “supply chain” operation, the defense federal acquisition regulation supplement (dfars) made specific cybersecurity protocols a requirement. Web last year, the department of health and human services’ (hhs) health sector cybersecurity coordination center (hc3) released a threat brief on the different types of social engineering 1 that hackers use to gain access to healthcare information systems and data. Target audience (community) comments point of contact informative reference submission form dependency/ requirement field name reference version
Web Joint Task Force Abstract This Publication Provides A Methodology And Set Of Procedures For Conducting Assessments Of Security And Privacy Controls Employed Within Systems And Organizations Within An Effective Risk Management Framework.
Web the ncsr question set represents the national institute of standards and technology cybersecurity framework (nist csf). This guide gives the correlation between 49 of the nist csf subcategories, and applicable policy and standard templates. Web security and privacy control collaboration index template ( excel & word) the collaboration index template supports information security and privacy program collaboration to help ensure that the objectives of both disciplines are met and that risks are appropriately managed. Prior to the 2.4 branch, a template functionality which allows users to create templates allows them to execute any code on the server during the bad filtration and old twig version.
Vulnerability & Patch Management Program.
Web this publication provides a catalog of security and privacy controls for federal information systems and organizations and a process for selecting controls to protect organizational operations (including mission, functions, image, and reputation), organizational assets, individuals, other organizations, and the nation from a diverse set. Web 0 1 2 3 4 5 6 7 8 9 10. This publication is available free of charge from: Federal information systems typically must go through a formal assessment and authorization process to ensure sufficient protection of confidentiality, integrity, and availability of information and information.
Security And Privacy Controls For Information Systems And Organizations.
By establishing a framework available to all, it fosters communication and allows organizations to speak using a shared language. Risk assessment csf v1.1 references: